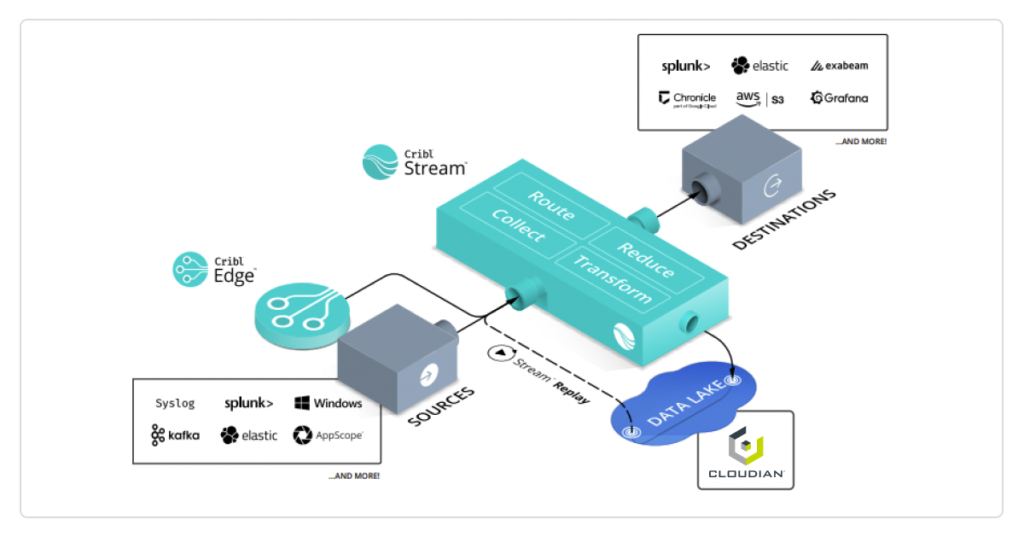
In today’s security and compliance landscape, organizations are drowning in log data. Cloud workloads, identity systems, EDR tools, firewalls, SaaS providers, and custom applications all generate massive volumes of telemetry—much of it required for compliance or threat investigations.
But here’s the problem:
Storing everything in your SIEM is no longer financially sustainable.
And archiving data in cold storage means analysts lose the ability to search or analyze it quickly.
This is the exact challenge a large financial services firm faced. Their data volumes were exploding, retention requirements were tightening, and SIEM costs were spiraling out of control. They needed a solution that could balance:
- Long-term retention
- Fast analytics
- Regulatory compliance
- Reasonable cost
The answer came from a modern data routing and observability pipeline: Cribl Stream and Cribl Lake.
Let’s break down how they solved their retention challenges—while actually improving security and analytics performance.
The Challenge: More Data, Higher Cost, No Visibility
Over an 18-month period, the organization’s daily ingest grew to over 8TB/day. Their analytics and security teams struggled with:
- Escalating SIEM Licensing Costs
Their SIEM charged by ingest volume. With current growth trends, the organization was projected to exceed their budget by $2.4M annually.
- Tightening Retention Requirements
Regulations like PCI-DSS, FFIEC, and internal policies required 1–7 years of log retention.
But SIEM indexing allowed only 30–90 days unless they purchased even more high-cost storage.
- Limited Access to Historical Data
Older logs were archived in cold storage, which meant:
- Slow or painful searches
- Multi-day retrieval times
- Dependency on Data Engineering
- Minimal access for fraud and compliance teams
Investigations involving long-term behavior or account activity could take 3–10 days to complete.
- Engineering Bottlenecks
To retrieve archived data, teams needed engineers to:
- Rehydrate terabytes of logs
- Normalize data
- Push logs into analytics tools
This was costly, slow, and created massive delays.
It was clear the organization needed a way to separate “hot” security data from “cold” compliance data—without losing the ability to search or analyze either.
The Solution: Cribl Stream + Cribl Lake
Working with NCI, the organization implemented a Cribl-based pipeline to route, reduce, and organize data intelligently.
Cribl didn’t just save SIEM costs—it completely reshaped their data strategy.
- Route the Right Data to the Right Place
Cribl Stream became the traffic controller for all log data.
Instead of pushing everything into their SIEM, logs were classified based on value:
|
Log Type |
Destination |
Why |
|
Authentication, EDR, firewall |
SIEM |
Needed for real-time detection |
|
Infrastructure logs |
S3 |
Useful, but not critical |
|
Verbose app logs |
Sampled + S3 |
High volume, low value |
|
Compliance logs |
Cribl Lake |
Must be retained AND searchable |
This approach reduced SIEM ingestion by 62%, instantly avoiding the $2.4M cost increase.
- Enable 7-Year Retention (Without Indexing Costs)
Cribl Lake provided the ability to:
- Store logs cheaply in S3
- Maintain full searchability for 7 years
- Support schema-on-read queries with Cribl Search
- Give teams direct access for analytics
Instead of relying on engineering teams to retrieve archived logs, analysts could now access data in seconds.
- Reduce Data Before It Hits Expensive Storage
Cribl pipelines cleaned and reduced logs before routing:
- Remove unnecessary fields
- Drop noise and debug logs
- Sample high-volume sources
- Normalize and flatten JSON
- Minimize event size
This drove a 40% reduction in average event size and further reduced storage costs.
- Unlock Analytics Across SIEM + S3 + Historical Data
With Cribl Search:
- SOC analysts investigated multi-year threats instantly
- Fraud teams analyzed long-term login and transaction patterns
- Compliance teams produced audit evidence rapidly
- No rehydration or ETL workflows were required
- Data Engineering overhead dropped to near zero
For the first time, all teams shared a unified analytics layer.
Why This Matters
Cribl allowed the organization to:
- Ingest less but analyze more
- Meet demanding retention requirements without premium SIEM storage
- Run long-term security investigations instantly
- Reduce SIEM cost exposure
- Scale data ingestion as logs grow
- Enable analytics across teams without bottlenecks