Vulnerability Remediation
Vulnerability Remediation Services — Close security gaps before attackers exploit them
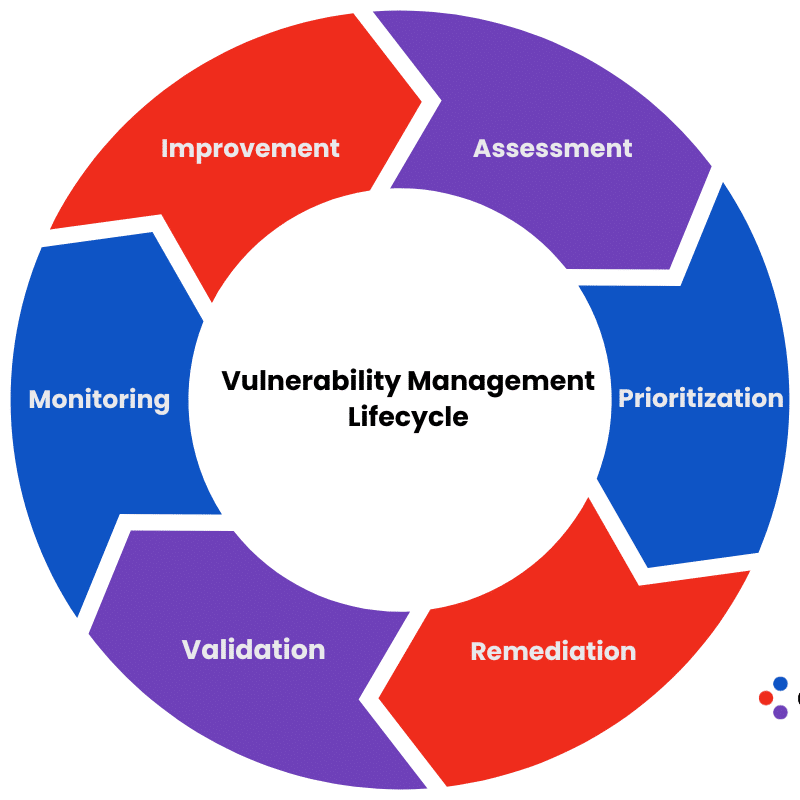
Finding vulnerabilities is only half the battle — fixing them quickly and effectively is what truly reduces risk.
At NCI, our Vulnerability Remediation Services turn assessment findings into real-world results.
We don’t just hand you a report — we partner with your IT and security teams to prioritize, patch, validate, and harden your systems for lasting protection.
Why choose NSecurity Consulting for remediation?
- End-to-end support — from identification to validation, we manage every stage of the fix.
- Prioritized by risk — we align remediation with business impact, focusing on what matters most first.
- Hands-on expertise — experienced engineers who understand both security and operations.
- Cross-platform coverage — Windows, Linux, network infrastructure, cloud, and applications.
- Verified results — all fixes are validated and documented for compliance and assurance.
- Seamless handoff — integrate with your existing ITSM or change management workflows (ServiceNow, Jira, etc.).
Our approach — practical remediation that fits your operations
1. Prioritization and planning
We start by reviewing your vulnerability assessment results and aligning them with asset criticality, exploitability, and business impact.
A remediation roadmap is created to guide your patching and mitigation efforts by priority and timeline.
2. Remediation execution
Our security engineers work directly with your IT and DevOps teams to:
- Apply security patches and firmware updates
- Reconfigure systems and network devices
- Update vulnerable libraries and third-party components
- Implement compensating controls where patching is not feasible
- Adjust permissions, access controls, and hardening baselines
3. Configuration and hardening
We benchmark your systems against industry standards (CIS, NIST, Microsoft Baselines, OWASP, DISA STIGs) and apply best-practice configurations to prevent reintroduction of similar vulnerabilities.
4. Verification and retesting
All confirmed fixes are documented with before-and-after evidence for compliance and audit readiness.
5. Reporting and continuous improvement
- Updated vulnerability status
- Verified fixes and residual risk
- Recommendations for continuous vulnerability management
- Insights for improving patching cycles and automation
Typical deliverables
- Remediation roadmap and work plan (prioritized and actionable)
- Change management documentation (ready for IT approval workflows)
- Before/after validation reports with evidence of resolved issues
- System hardening checklist and baselines
- Lessons-learned summary and optimization guidance
Integration with existing tools
We integrate remediation workflows with your existing platforms, including:
- Ticketing systems: ServiceNow, Jira, Freshservice
- Patch management: SCCM, WSUS, Intune, Ansible, Qualys Patch, Tanium
- CI/CD pipelines: GitHub Actions, Jenkins, GitLab CI
- Monitoring: SIEM, SOAR, and vulnerability scanners for verification
Benefits to your organization
- Reduced attack surface: Close exploitable gaps before they’re weaponized.
- Operational efficiency: Align remediation with IT maintenance cycles.
- Improved compliance: Verified remediation supports PCI DSS, HIPAA, and ISO 27001 requirements.
- Stronger security posture: Continuous hardening builds resilience over time.
- Peace of mind: Validation ensures vulnerabilities are truly eliminated.
Who benefits
- Organizations that have completed vulnerability or penetration testing
- Enterprises struggling with patch backlogs or configuration drift
- Cloud and hybrid environments needing continuous validation
- Compliance-driven industries: healthcare, finance, and critical infrastructure